Table of Contents
ToggleIntroduction
In the modern digital world, data has become very crucial in organizations. It has become a regulatory and business imperative to safeguard it. However, although encryption protects the information in storage or transit, it is most often used when it is being processed. So, what is
confidential computing? It is a radical method that ensures the security of information during the use process, which does not allow even administrators or cloud providers access to it. This innovation is a critical change in knowing what is confidentiality in computer security.
Through this article, you will get to know how does confidential computing work and how important is establishing a trusted environment in which things are processed, giving businesses privacy as well as freedom of innovation.
If you’re also curious about evolving IT roles, you may want to read about what a DevOps Engineer does.
The Rise of AI and the Need for Security
To understand what is confidential computing, you have to know that Artificial Intelligence also works best with extensive datasets, most of which contain sensitive data. Lack of proper protection would cause organizations to expose valuable or regulated information.
With the utilization of confidential computing Azure, businesses are able to feed data into AI-based models without ever disclosing unprocessed records. This would facilitate collaboration between hospitals, banks, and researchers and still maintain privacy.
To see how AI itself is evolving, check out what Agentic AI is.
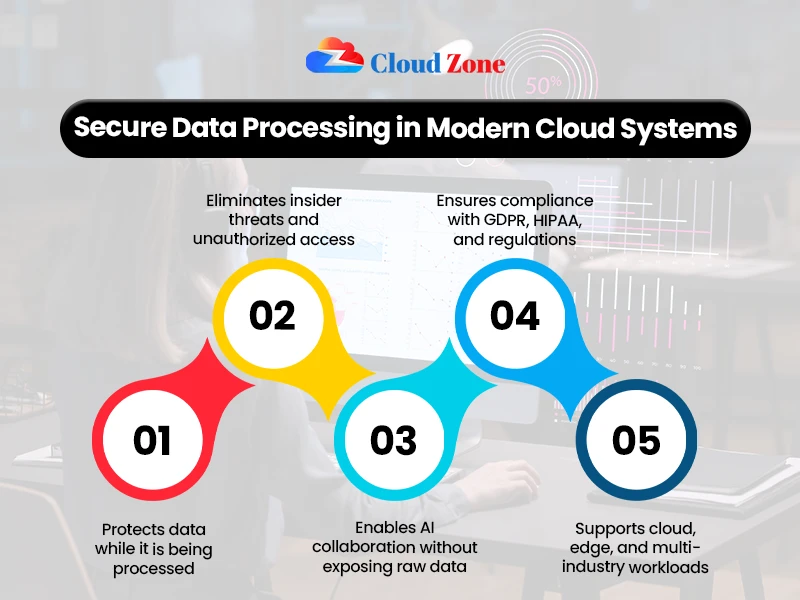
Benefits of Confidential Computing for AI
- Enables collaborative training of AI between organizations without dataset exchange.
- Eliminates the exposure of confidential or controlled information in the process.
- Adheres to the strict rules, including GDPR and HIPAA.
- Minimizes the insider risks, as the administrators will not be able to see the data.
- Develops trust, which will promote the adoption of AI in industries more rapidly.
- This illustrates how confidential compute transcends beyond a protection; it is an innovation facilitator.
How Does Confidential Computing Work?
The fundamental principle of this technology is Trusted Execution Environments (TEEs). These enclaves build safe areas in a processor to which sensitive tasks are segregated. Information is fed in encrypted, processed secretly, and fed out encrypted.
Developers secure the system carefully; moreover, they ensure that unauthorized users cannot access internal data even with system privileges. This is how does confidential computing works and how confidential computing bridges one of the biggest security vulnerabilities in the online infrastructure.
And to understand how monitoring fits into security models, you may find Amazon CloudWatch useful.
Real-World Applications
- Healthcare: Hospitals do not reveal identities when analyzing patient data.
- Finance: Banks’ cooperation: Banks work together on the detection of fraud and record maintenance.
- Government: Defense agencies are processing workloads that are classified in commercial clouds.
- Retail: Stores make experiences personal in such a way as not to store raw customer logs.
- Academia: Researchers combine datasets carefully; moreover, they ensure confidentiality and therefore prevent any violations during the process
Shield critical workloads with hardware-grade privacy — simple, powerful, and efficient.
Cloud Adoption: Why Enterprises Need It
Now, the cloud is the driver of digital transformation. However, businesses have been reluctant to shift important loads of work due to a lack of trust. How can the security of data be ensured in case it is hosted on the servers of a different person?
In this case, the solution is in this computing. It guarantees that the data is not visible to the
cloud providers themselves, so that even the most sensitive tasks will be safe when using the cloud.
If you want to know more about deployment models, take a look at Hybrid Cloud.
Azure Confidential Computing
- Secures workloads of Microsoft administrators and third-party threats.
- Facilitates adherence to healthcare, financial, and government policies.
- Migrates old applications to enclaves with little redesigning.
- Gives examples in the industry: medical analytics, fraud prevention, and supply chain security.
Using Azure confidential computing, organizations have the advantages of the flexibility of cloud services, but privacy is not compromised. This renders confidential computing Azure an important secretarial instrument to regulated industries.
To upskill in such areas, AWS Skill Builder is a great place to start.
Looking Ahead: Confidential Computing Conference 2025
The next breakthroughs in the field will be in the limelight at the Confidential Computing Conference 2025. The discussion will cover cross-cloud compatibility; moreover, it will include hardware performance and integration with emerging technologies like Web3.
The other theme will be quantum readiness, getting ready enclaves so that they cannot be decrypted by quantum computers in the future. The occasion will be an expression of the fact that what is confidentiality in computer security has been progressing as a worldwide benchmark of assurance.
If you’re interested in broader cloud adoption tools, check out this complete guide to OneDrive.
Confidential computing gives you total control over sensitive cloud workloads.
Beyond the Hype
- Secures information in use and not only when at rest or in transit.
- Banishes insider threats by concealing information from administrators.
- Eases the burden of privacy laws.
- Promotes teamwork through safeguarding collective analytics.
- Eliminates the need to use expensive and tailored security layers.
These benefits demonstrate that what is confidential computing is more than a myth; it is the basis of safe digital ecosystems.
And when paired with cultural practices like DevOps culture, its benefits multiply.
Confidential Computing for Edge Devices
With the growth in the use of IoT and edge devices, it is essential to protect data closer to the origin. In fact, the cars and medical devices, as well as the smart sensors, generate personal data, which needs to be kept safe.
Expanding the use of confidential computing to edge computing systems can surely help autonomous vehicles analyze navigation safely, factories safeguard the data about their operations, and biometric devices can process biometric information without revealing the identity of their users.
For a deeper dive, you can read about Edge Cloud Computing.
Cross-Border Collaboration
- The system safely performs risk modeling; moreover, it detects fraud efficiently and therefore protects organizations from financial threats.
- Helps global supply chains be analyzed securely by multinational firms.
- Enables the sharing of intelligence between governments without having to reveal raw data.
- Providing support to the data sovereignty regulations across borders.
- Favors shared innovation by breaking down the barriers to mistrust.
This renders confidential computing, Azure, and other related services indispensable to organizations that are situated at the international level.
Industry-Specific Opportunities
Healthcare: Keeps the records of the patients safe when discovering drugs or diagnostics.
Finance: The system enables risk modeling and fraud detection; moreover, it performs these tasks safely and efficiently.
Retail: Protects the personalization strategy for customers.
Government: Deals with sensitive loads such as census or defense information.
Energy: Achieves partnership in the clean energy research and grid optimization.
These cases point out the fact that this computing is viable, extensible, and effective in industries.

Conclusion
So, what is confidential computing? It is surely a breakthrough in securing data at its most vulnerable stage: while in use. It leverages trusted execution environments and encryption; therefore, it keeps sensitive workloads private and moreover ensures security wherever they are processed..
Further, with the rapid growth of AI, global collaboration, and cloud adoption, this technology is fast becoming essential. Platforms like Azure confidential computing are proving its real-world value, while events like the confidential computing conference 2025 signal how far it will go.
Ultimately, this computing represents a new era of confidentiality in computer security, one where innovation and privacy finally go hand in hand.

Sukhamrit Kaur
Sukhamrit Kaur is an SEO writer who loves simplifying complex topics. She has helped companies like Data World, DataCamp, and Rask AI create engaging and informative content for their audiences. You can connect with her on LinkedIn.




