Table of Contents
ToggleIntroduction
In today’s digital world, it is essential to gain access to systems and data. Therefore, learning what is Identity and access management provides that the correct people can get to the correct resources at the correct point in time. Besides, IAM (Identity and Access Management) helps companies avoid unauthorized access, preserve confidential data, and simplify operations.
Different knowledge about what is identity and access management IAM enables organizations to develop effective security measures and remain compliant in a complicated IT infrastructure.
Moreover, this article helps to get a clear perspective on what IAM is and what its major elements are, and how to practice best practices to develop more robust security approaches and be compliance-driven in the modern and evolving world of IT.
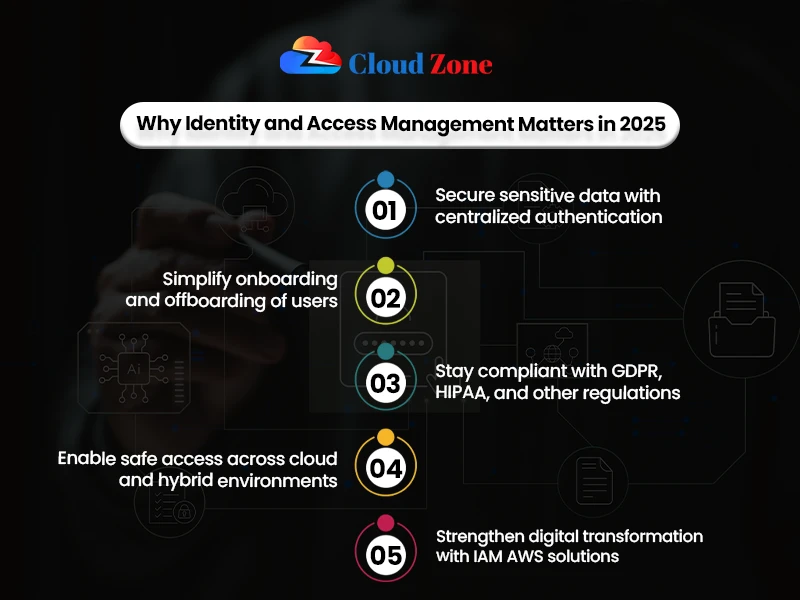
The Fundamentals of Identity and Access Management
Firstly, to understand the fundamentals, you need to know what is Identity and Access Management is a model that authenticates user identities, permission controls, as well as tracks access within systems. Besides, it is secure and efficient in terms of operations.
Key benefits include:
- Firstly, securing sensitive information against unauthorized access.
- Secondly, making the user onboarding and offboarding simpler.
- Thildly, observing policy regulations.
- Lastly, outsourcing IT to save money.
Moreover, using IAM (Identity Access Management), companies can implement a control mechanism that enables internal teams and external partners to access only authorized resources.
With cloud adoption growing rapidly, AWS is set to invest an additional $2 billion in Indian data centers, making IAM even more vital for managing secure access.
Manage authentication, authorization, and roles efficiently while reducing security risks across environments
Core Components of Identity and Access Management IAM
Firstly, it is necessary to understand the essence of what is identity and access management IAM AWS to master its core components. Moreover, authentication is the process of ensuring that the user claiming to be something they purport to be is indeed who they purport to be, through passwords, tokens, or even biometrics. Consequently, the processes of authorization specify access permissions of a validated user. User Lifecycle Management is an automated process of onboarding, offboarding, and role modifications.
Then, Audit and Reporting logs all access to events to comply, and Directory Services is the central location of user identities and credentials. Hence, all of these elements can facilitate safe operations on the cloud and on-premises, such as IAM AWS implementations.
When exploring secure file access and sharing, tools likeOneDrive integrate with IAM principles for identity-based permissions.
Why Organizations Adopt IAM AWS
The use of cloud infrastructure becomes very essential in organizations, and hence, identity and access management IAM AWS becomes paramount. Besides, cloud-native IAM provides secure access to distributed systems and allows the following features:
- Application single sign-on (SSO).
- Multi-factor authentication to provide security.
- Single-point policy implementation on platforms.
- The international standards, such as GDPR and HIPAA.
Also, application of IAM in the cloud cover environment enables organizations to ensure safety in addition to the support of the digital transformation plans.
To skill up, professionals can leverageAWS Skill Builder and gain knowledge about IAM AWS implementations.
Customer Identity Management with CIAM
Customer Identity and Access Management (CIAM) is a system that deals with the security requirements of external users. In addition, CIAM is privacy-oriented, user-oriented, and convenient, as compared to internally-oriented IAM.
CIAM solutions provide:
- Safe log-in and self-service account management.
- Social authentication and password-less.
- Surveillance to combat fraudulent account transactions.
- Consent and privacy management: Regulatory compliance.
Also, the incorporation of CIAM can help organizations to secure customer information as well as establish trust and relationships.
IAM also supports monitoring capabilities similar totelemetry, helping track user activities and unusual behaviors.
Cloud Identity Solutions Explained
They provide centralized authentication for users in both cloud and hybrid environments. It makes accessing easier, enhances security surveillance, and eases the process of complying.
In addition, these services enable organizations to administer employees, contractors, and partners on the same platform. Besides, single sign-on will minimize password fatigue, and the centralized monitoring will ensure that security teams identify potential threats. Also, Cloud identity, coupled with other IAM solutions, offers flexibility and control to organizations, which ensures the security of access to all IT assets.
Organizations today adopt IAM alongside hybrid cloud strategies to ensure unified access control across environments.
Best Practices for Identity and Access Management
A good identity and access management involves the presence of clear policies and constant monitoring. The principle of least privilege, the use of multi-factor authentication, and auditing the user permissions should be implemented and regularly carried out in organizations. The implementation of the IAM with the security surveillance applications and educating the staff on the security of their identity will maintain the security and efficiency.
It is also important to regularly revise IAM policies and make them compliant. Organizations can enhance security further by automating the identity lifecycle management, utilizing role-based access controls (RBAC), and embracing the concept of zero-trust. Technology, processes, and user awareness are what
can be used to build a robust IAM system that is flexible to changing cyber threats.
Integrations with monitoring tools such as Amazon CloudWatch make IAM more powerful by correlating access logs with infrastructure events.
Challenges in Identity Access Management
The problem is that organizations encounter difficulties in using these solutions.
The process of integrating legacy systems and current IAM systems may not be easy. Organizations are forced to strike a balance between security and user convenience, handle identities between and among a variety of cloud providers, and stay regulatory compliant. The misconfigurations and insider threats are also dangerous factors, and governance and monitoring are important elements of a successful IAM strategy.
The DevOps culture benefits from IAM by ensuring secure, role-based access for development and deployment teams.
Prevent breaches by controlling identities across applications, devices, and networks
Trends in IAM
This has a future that is propelled by new technologies:
- Analytics of abnormal behavior based on AI.
- Single-Click secure and convenient logins.
- Dynamic access control with biometric and adaptive authentication.
- Granting access to Zero Trust security frameworks with permissions granularity.
- Cloud-native, scalable, and flexible IAMs.
These innovations ensure that IAM is more responsive, safe, and convenient to the user, and in line with the emerging cyber threats.
For professionals, AWS security training is essential to properly implement IAM best practices.
Evaluating an IAM Solution
The choice of the IAM solution has to be attentive. The organizations have to evaluate multi-factor and adaptive authentication, integration capabilities, audit and reporting features, and scalability. The selection of the appropriate solution can guarantee a high level of security, efficiency of the operations, and an enhanced user experience. Properly implemented IAMs secure important data and allow for the development and digitalization.
Benefits of IAM
- Firstly, deterrents of unauthorized access and security breaches.
- Secondly, it makes user management easier and minimizes the IT overhead.
- Thirdly, maintains industry/legal standards.
- Also, it enhances the user experience and the process of authentication.
- Lastly, it supports the secure operation both in the cloud and in the on-premises environment.

Conclusion
To conclude, the number of cyber threats is on the increase, and learning what is identity and access management IAM AWS is essential to secure sensitive data and facilitate digital
transformation. Also, regardless of overseeing in-house teams, applying CIAM, or IAM AWS, companies can safeguard resources, maintain adherence, and deliver a smooth customer experience.
IAM not only minimizes security risks but also enhances efficiency in operations because authentication and access control are centralized. In addition, through modern IAMs, business organizations will be able to simplify the user onboarding process, improve audit trail transparency, and create customer trust by providing secure and convenient accessibility.
Learners in India can upskill by enrolling in top cloud computing institutes in Chandigarh to strengthen IAM and cloud expertise.
Improve the security position of your organization. Explore identity and access management, IAM identity access management, and cloud identity solutions. Elevate access, secure vital information, and provide access to users throughout your enterprise. Begin to put scalable and efficient IAM into practice.

Sukhamrit Kaur
Sukhamrit Kaur is an SEO writer who loves simplifying complex topics. She has helped companies like Data World, DataCamp, and Rask AI create engaging and informative content for their audiences. You can connect with her on LinkedIn.




